How to Perform Information Management Risk Assessments

The goal of a risk assessment is to understand the risk to organizational operations and organizational assets. You must determine how your organization profits, how various assets affect the profitability of the business, and what risks could potentially lead to large monetary losses. After performing an information management risk assessment, you’re prepared for enhancing your infrastructure and reducing the risks most likely to preface financial loss.
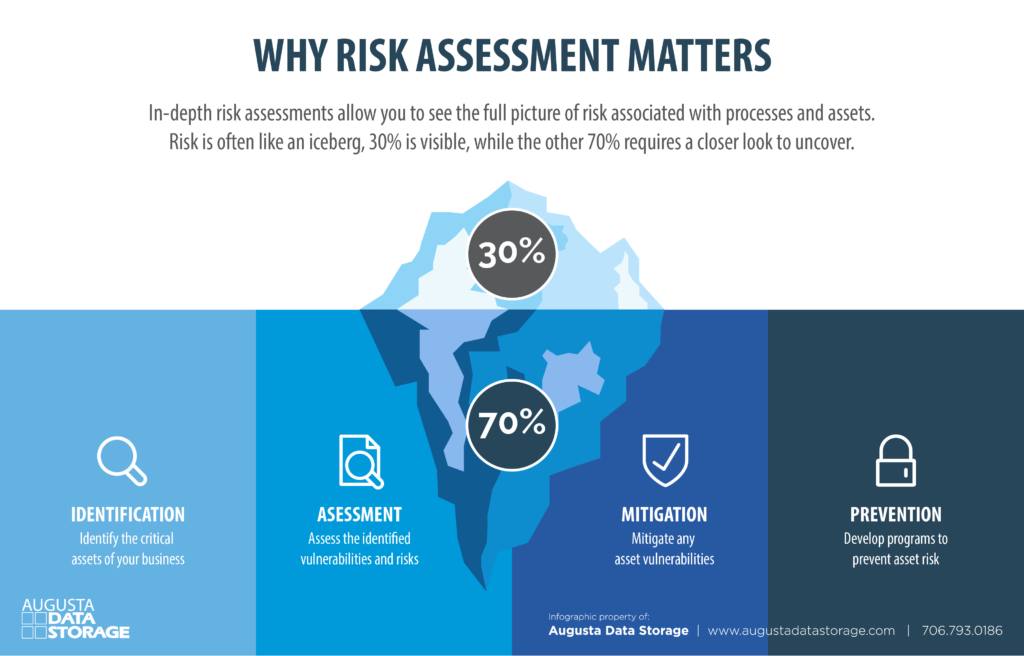
Steps to Risk Assessment
Carrying out risk assessments allow organizations to make informed decisions concerning resource allocation, tooling, and security control implementation. The four steps to successful security risk assessment include Identification, Assessment, Mitigation, and Prevention.
1. Identification: Identifying all critical assets.
2. Assessment: Assessing vulnerabilities and risks.
3. Mitigation: Mitigating asset vulnerabilities.
4. Prevention: Preventing asset risks.
Completing annual risk assessments poises your organization for emergency response and recovery, reducing the chances of data loss, compromised information, or worse.
Primary risk factors for information security
The rapid advancement of technology and the emergence of new threats in the digital world have made information management risk assessment a critical component of any business’s security strategy. There are several primary risk factors that organizations must consider when carrying out their information management risk assessments.
These include
- increased reliance on cloud-based technologies,
- BYOD policies
- cyber attacks and data breaches
- rising complexity of compliance with regulations such as GDPR and HIPAA
- employees or contractors with access to sensitive data
- vulnerabilities associated with third-party vendors or service providers that store organizational data on their systems
- emerging risks posed by artificial intelligence (AI) and machine learning technologies
- lack of understanding and education on risk factors and preventative measures
- vulnerabilities of remote workforce and remote information access
By understanding these key areas of potential risk exposure – along with other emerging trends – businesses can ensure they are taking adequate steps to protect their assets against future threats.
Best practices for information management of hard copy records
As organizations grow, their reliance on physical paper records to store sensitive data increases. Properly managing hard copy records is essential for complying with regulations and avoiding costly data breaches. To ensure that all hard copy documents are properly managed and securely stored, it’s important to follow best practices for information management of hard copy records.
As your organization works to improve information management systems, consider implementing these best practices:
- Develop a formal document retention policy and establish procedures for securely storing documents.
- Regularly monitor access to the physical records and ensure that only authorized personnel have access.
- Ensure all hard copy documents are stored in secure locations such as locked filing cabinets or fireproof safes.
- Perform regular inventory checks of the hard copy documents and ensure that only relevant documents are being stored.
- Create a clear chain of custody for your records and information
- Implement a secure destruction process for disposing of documents that are no longer needed, to prevent them from falling into malicious hands.
Best practices for information management of digital records
In the digital age, information management systems are essential for businesses to protect their sensitive data and comply with regulations. Properly managing digital records is just as important as hard-copy documents, and organizations should take steps to ensure that all digital records are securely stored and managed. To help streamline your processes, here are some of the best practices for effectively managing digital records within your information management systems.
- Create separate user accounts and passwords for each employee with access to the system.
- Ensure that only authorized personnel have access to digital records.
- Conduct regular audits of your information management systems, tracking who has accessed or modified files.
- Encrypt all data stored in the system, and use secure protocols when transmitting information over networks.
- Always back up data in multiple secure locations, cerating layered backup systems.
- Implement two-factor authentication for logging into the system and accessing files.
- Use software that can detect and alert you of malicious activity or potential security threats.
- Update your information management systems regularly to ensure they are secure against new cyber threats.
- Regularly review policies and procedures, and train employees on proper information management practices.
Layered backup systems help protect information systems against damage and loss
A layered backup system is an approach to data protection that uses multiple layers of backup to ensure that critical information assets remain secure. It involves the use of both on-site and off-site backups, with different technologies used for each layer. This allows organizations to protect against a wide range of potential threats, from natural disasters and power outages to malicious attacks, ensuring that data is preserved and available when needed.
Layered backup systems offer numerous benefits for businesses, such as improving the speed of recovery after a disaster strikes and reducing the risk of lost or corrupted data. They also provide greater flexibility in terms of where and how backups are stored, allowing organizations to tailor their backups to their specific needs and requirements.
By implementing a layered backup system, organizations can ensure that critical information assets remain secure and available when needed, giving them peace of mind knowing that their data is safe and sound. A layered backup system can be the difference between surviving a disaster or experiencing catastrophic data loss, so it’s essential to create one that is tailored to the specific needs of your organization.
Data retention policies ensure the appropriate management of information systems through a designated destruction date
Organizations must have clear and effective data retention policies in place in order to ensure compliance with applicable laws and regulations. These policies define how long certain types of data should be retained, when that data can be destroyed, and who is responsible for data retention. It’s important to create a consistent set of rules and procedures for handling data, as well as an audit trail for tracking any changes.
Data retention policies should also define who has access to the information, how it can be used, and whether it can be shared with third parties. By having clear policies in place, organizations can ensure that data is properly managed and secured, preventing unauthorized access or accidental deletion.
Effective data retention policies are essential for any organization looking to maximize its information security. They provide a level of consistency and clarity when it comes to managing digital records, ensuring that all personnel handling sensitive information are compliant with applicable laws and regulations. It’s important to review your policies regularly to ensure they remain effective and up-to-date.
Secure Storage Services offer increased protection for your digital and hard copy records
Augusta Data Storage offers fundamental services as remedies to the numerous risks and vulnerabilities affecting information management today, ensuring your data remains safe and accessible to you 24/7 in the event of an emergency. Our secure climate-controlled vault allows us to safely store your critical data off-site and offline, with easy-to-use barcode tracking and flexible delivery features. No matter the format, we’ve got secure and accessible options for your peace of mind.
For clients in healthcare, legal, and financial service industries requiring hardcopy management, take advantage of our scan-on-demand services. Augusta Data Storage offers storage and immediate access to hardcopy records. Simply make a request for retrieval and our team will locate and securely deliver the data to you. Whether your organization is looking to store records or create backups, our state-of-the-art facilities and secure ease of access options are sure to meet your requirements.
Human error, system failure, and natural disasters like fires, floods, and tornadoes- these are the hazards invariably facing data security. Performing information management risk assessments prepares you for the worst, saving your data (and perhaps even your organization) from the unexpected. Mitigate the risks involved and secure your critical assets by creating copies across secure online, offline, and off-site systems.
DISCLAIMER: The information contained in this article is a collection of best practices across various industries. When completing a risk assessment for your organization, it is best to seek the guidance of an industry-specific compliance officer and governing body.
