Information Security 101: Understanding the Foundations of Records Information Management Policies

When we say “document security” or “information security” what are we really talking about? What is involved? Why is it important? How can you ensure security? For us, it’s about data protection. This includes protecting the privacy, intellectual property, and personal information security of both you and the clients with whom you do business.
Why is Records Information Management (RIM) Important?
Creating a RIM process means that you have to develop a trackable paper trail that leads to safe and secure storage or destruction of the proprietary information that your company possesses. We often find the reason that our customers are hesitant to build and develop a RIM process is that they fear the unknown; are unwilling to confront the consequences of their inaction (HIPPA). They manage their business in the short term with no forethought to the “what ifs” that exist when talking about information management; and most likely, failure to adapt to change and implement new policies and practices. But what do we stand to lose if we don’t manage these processes? At most, we are looking at a large-scale data breach and at the least, you run the risk of some small portion of the information ending up in the wrong hands (think identity theft or credit card fraud, etc). If you’re considering developing a Records Information Management process, do you know what the options are and what to look for in a service provider?
What does Records Information Management Include?
Use these tips to strengthen your existing records information practices. If you are developing a new Records Information Management process you will want to consider several factors in your information management timeline.
- Records Storage: How will you store active documents that you must have access to on a daily basis? How will they be kept secure? How long will you keep these items in storage?
- Records Archiving: If you have documents that you may need to keep archived but do not need on a daily basis, what is the process for moving them from active storage to the archives, how are they protected and managed during the process? What is the security in the archived records storage area? What is the process for retrieving records from the archives? Who has access to these records?
- Records Purging: When records become out of date or reach the end of their useful life what is the process for removing them from your archives? How often will you purge documents? Annually? Bi-Annually? And how will you track what to purge and when?
- Records Destruction: What happens to the purged documents? Do you toss them in the garbage or do you have a safe and secure way to ensure their destruction? What are the document destruction steps?
- Digital Information Security: We aren’t just talking about paper information, what happens to old computers, tapes, discs, and other digital devices that store information? What processes do you have in place to manage these devices and keep them secure?
- Employee Education: Do your employees know the risks? Do they know the steps to take in day-to-day operations to protect information? Incorporate your cyber security training as a part of the onboarding process.
Records Information Management Document Lifecycle
Records Information Management (RIM) is the practice of managing the records for your organization throughout its lifecycle. This means from the time they are created until their disposal. So, what does that entail?
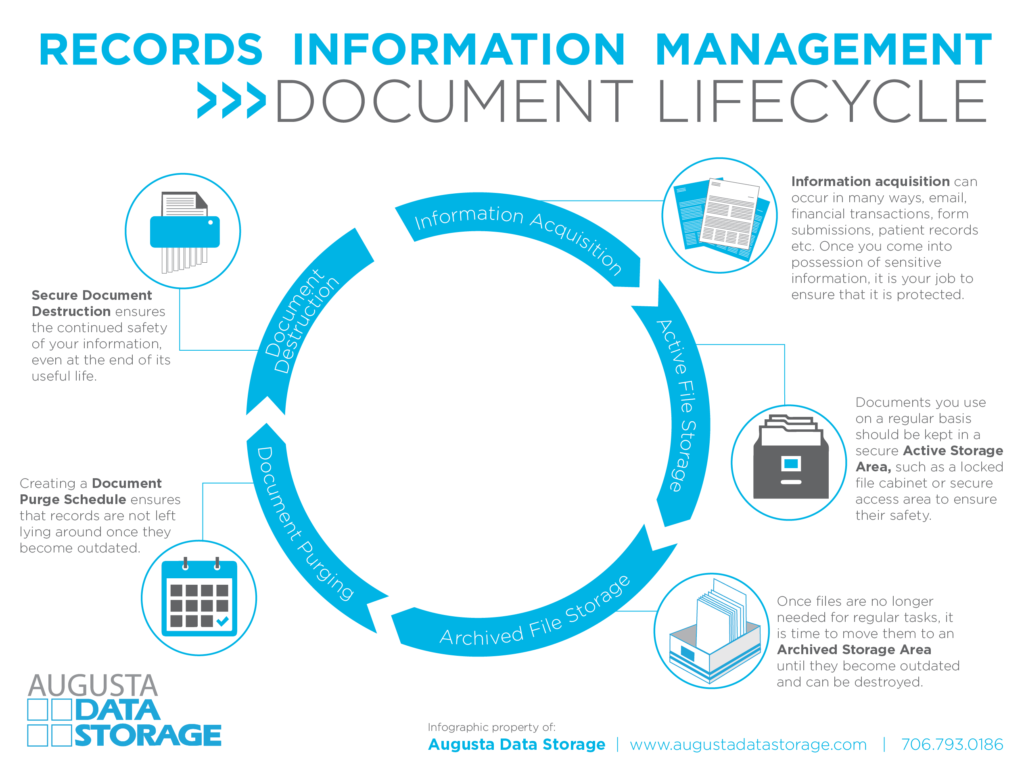
Information Acquisition
Information acquisition can occur in many ways: email, financial transactions, form submissions, patient records, etc. Once you come into possession of sensitive information, it is your job to ensure that it is protected.
Distribution & Storage
Records should be categorized according to how sensitive the information is to ensure the best security. Different records must be held for a certain amount of time according to privacy and information laws and compliance requirements in your industry segment. Records are stored depending on how accessible they need to be: active files and archived files.
Active File Storage
Documents you use on a regular basis should be kept in a secure Active Storage Area, such as a locked file cabinet or secure access area to ensure their safety.
Archived File Storage
Once files are no longer needed for regular tasks, it is time to move them to an Archived Storage Area until they become outdated and can be destroyed. Data backup processes are crucial to ensure that records are always accessible.
Document Purging
Creating a Document Purge Schedule ensures that records are not left lying around once they become outdated. Records typically have a specific retention period. Be sure your records retention policy is effective and up to date.
Document Destruction
Secure Document Destruction ensures the continued safety of your information, even at the end of its useful life.
When developing a Records Information Management process you will need to consider all these moving pieces and develop a plan for how information and data will be handled on a day-to-day basis. Be sure to note both short-term and long-term storage requirements, as well as destruction requirements. There are many things to take into consideration so it might be worth considering a records management partner.
What is a Records Management Partner?
When you’re dealing with a large variety of information, sometimes it’s better to bring in a team of people who can help outfit custom solutions for your organization’s unique needs, and that is where Augusta Data Storage comes in. Imagine having a records management partner to help you organize, store, retrieve, refile, purge, and destroy information based on your records information management plan.
We offer secure storage for documents and a climate-controlled vault for items that require specific storage conditions like tapes and electronic devices. In addition, our team can offer:
- Document Scanning and Imaging services
- On-site or off-site secure shredding services
- 24/7 Login-software access
- Barcode tracking and location storage
- Document Retrieval service
With over 25 years of records management experience, our process is constantly growing and evolving to ensure that we are able to protect your information and assets as technology and the way you do business continues to change.
Finding a Record Storage Partner
When you’re looking to find a partner to help manage your information security, make sure you do your due diligence. Look into your third-party providers, know who is coming into your facility and how they are handling and managing your information. Look for companies who are certified with organizations like PRISM, ARMA, and NAID, and make sure you are managing your information within your own facility.

Do’s and Don’ts of Information Security
- Don’t leave critical paper out in the open
- Don’t use open recycling bins or cans that anyone can access
- Don’t place confidential information in outdoor garbage bins
- Do limit employee access to secure information (locking file cabinets, secure areas, password protected files)
- Do institute a clean desk policy to avoid papers falling prey to wandering eyes.
- Do use lockable shred bins or cabinets
- Do research any 3rd party groups that will handle or manage your information
- Do put a data breach action plan in place as a precaution.
